Table of Contents
1. Introduction
I encounter many video hosting providers advertising so called basic DRM solution. Main purpose is to block downloading videos. After quick analyze I realize it is not true and it’s only misleading people cause they might associate basic DRM with real one that is costly. I am using bunny net video hosting so I will explain mechanism based on it.
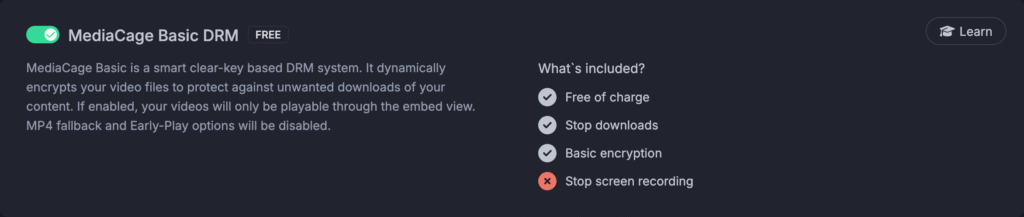
Bunny net offers MediaCage Basic DRM protection. They promising:
- stop downloads
- Free of charge
- Basic encryption
I agree that I do not need to pay and there is encryption, not sure why they claim basic encryption. In fact they using Advanced Encryption Standard (AES) so why not shine in marketing brochure and keep that name? For me unbreakable algorithm that is industry standard is strong enough. Reasonable distinction is weak/strong and here of course no one should dare to propose weak keys or algorithms. Anyways let me focus on most important point out there – stop downloads. Is that true?
2. Reverse engineering
With DevTools (F12) you can easily see all video chunks and AES key
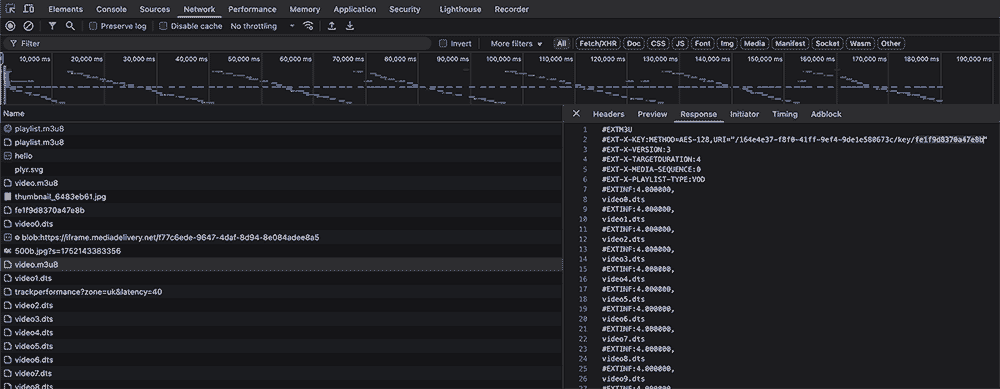
By right click on key file you can generate curl command that will let you download it to local storage. Then using script you can download end decrypt all video fragments separately.
#!/bin/sh
# Downloading the key
curl 'https://vz-77cdd36a-bab.b-cdn.net/164e4e37-f8f0-41ff-9ef4-9de1e580673c/key/fe1f9d8370a47e8b' \
-H 'Referer: https://iframe.mediadelivery.net/' \
-o key.bin
KEY_HEX=$(xxd -p key.bin | tr -d '\n')
# Download chunks encrypted (AES128)
# end decrypt them
for x in {0..139}; do
curl "https://vz-77cdd36a-bab.b-cdn.net/164e4e37-f8f0-41ff-9ef4-9de1e580673c/1080p/video${x}.dts" \
-H 'Referer: https://iframe.mediadelivery.net/' -O
IV_HEX=$(printf "%032x" ${x})
openssl aes-128-cbc -d -nosalt -K $KEY_HEX -iv $IV_HEX \
-in video${x}.dts -out decrypted_${x}.ts
done;
NOTICE: number of chunks will vary from video to video.
After downloading you can merge them to play.
# Merge them into one plus convert to mp4
cat decrypted*.ts > merged_decrypted.ts
ffmpeg -y -i merged_decrypted.ts -c copy merged_decrypted.mp4
3. ffmpeg tool
This tool can decrypt easily videos as long as it can access decryption key.
Because decryption key is explicitly mentioned in m3u8 playlist file – EXT-X-KEY
you can just pass playlist as input. REMEMBER about Referer
cat video.m3u8
#EXTM3U
#EXT-X-KEY:METHOD=AES-128,URI="/164e4e37-f8f0-41ff-9ef4-9de1e580673c/key/fe1f9d8370a47e8b"
#EXT-X-VERSION:3
#EXT-X-TARGETDURATION:4
#EXT-X-MEDIA-SEQUENCE:0
#EXT-X-PLAYLIST-TYPE:VOD
#EXTINF:4.000000,
video0.dts
Command to download “Basic DRM” protected video from bunny net.
ffmpeg \
-headers "Referer: https://iframe.mediadelivery.net" \
-user_agent "Mozilla/5.0 (Macintosh; Intel Mac OS X 10_15_7) AppleWebKit/537.36 (KHTML, like Gecko) Chrome/136.0.0.0 Safari/537.36" \
-i "https://vz-77cdd36a-bab.b-cdn.net/164e4e37-f8f0-41ff-9ef4-9de1e580673c/1080p/video.m3u8" \
-c copy 164e4e37-f8f0-41ff-9ef4-9de1e580673c.mp4
4. Other providers vs bunny net
I checked Hotmart video player and noticed they using hmac for signing URLS together with AES encryption of video chunks – that’s slightly better but still key is accessible and mentioned in playlist content which effectively make video easily downloadable. Problem with bunny net is they disable signing URLs when you enable basic DRM. I got response from their service desk “Cannot have Token authentication and DRM enabled at the same time.”
Therefore currently enabling basic DRM make it less secure because all video fragments can be directly downloaded from Pull Zone without any protection. “Allowed Referer” can be spoofed. It is better to disable basic DRM and enable CDN token authentication. At least files won’t be exposed without token through Pull Zone.
So from security perspective they are similar once you turn off useless basic DRM.
5. Conclusion
Today some video providers came with basic DRM solution. In fact they are delivering video chunks in encrypted format along with AES key. Therefore whoever can play video can also easily decrypt it. Word MediaCage(bunny) is misleading too, real DRM keep AES keys protected so user cannot access them. Encryption does not make sense if AES key is publicly available via same non-secured non-signed Pull Zone URLs. Therefore title of this article I will dedicate especially for all video hosting providers to stop promoting nonsense solution. You as user just stop using it as it does not make sense and unnecessarily using more CPU resources during decryption. For wordpress I and bunny net I recommend you using plugin that automatically generate tokens for video content making it protected from unauthorized embedding – see tools section or access it directly.