Table of Contents
1. Introduction
You may already heard about crime stories of drug kingpins who were trace and arrested even they were using TOR network. Why it happened to them? Because they weren’t very careful. In this article I am going to show you example when you will use TOR web browser to download PDF file and that will be the trap. Let’s start.
2. Connect to TOR network
Easy way to start exploring internet via TOR is to start up TOR web browser.
Then open up URL address of this blog post. Then download below PDF file.
3. Open with Adobe Reader
You can download Adobe Reader tool to view PDF. This tool is good example because it handles extra media embedded in PDF file like sound, videos, javaScript and more. Therefore there is a risk to download content using your IP address instead of TOR node. I prepared file in this way that it has a picture and once you click on it with enabled content it connects to webhook leaving trace back to your origin IP address. This is because Adobe Reader is not configured to connect to internet via TOR network.
This is very important step to understand. Anything you download from internet via TOR not necessary will continue to use that style of communication.
# Webhook URL - will expire after some time
https://webhook.site/#!/view/ca3ac18d-c158-46d3-9143-30ca8b71c46a/13cf3715-ddec-4933-b86f-dd4954a89f56/1
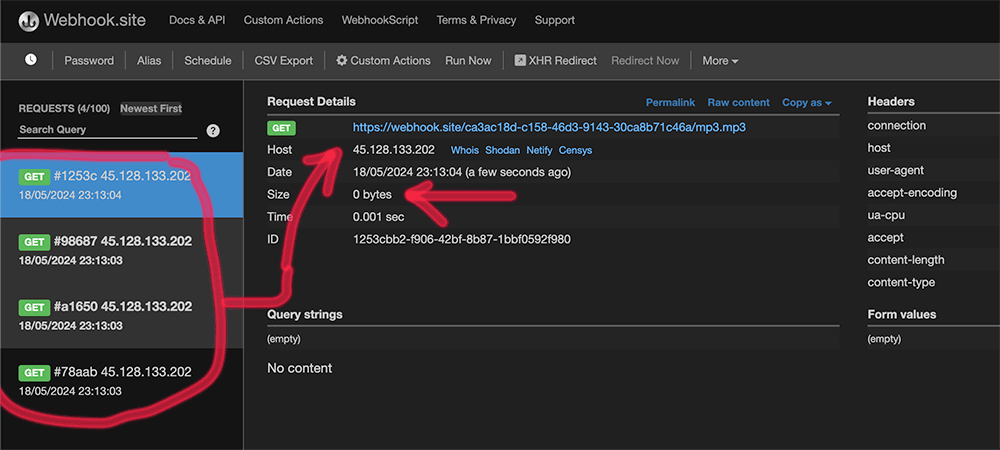
You can see below that accessing media does not show anything because media URL points to non-existing file, anyways connection is done and that’s enough.

Connection to potential external resources is established. Your IP address is visible here.
4. More safe alternative
As a remedy I propose you to use dangerZone tool that was design to remove any unsafe content from PDF files and let user display safe version. This let you convert any downloaded document in few popular formats into non-interactive file.
4.1. Converting downloaded PDF
Dangerzone has simple dialogue that let you choose your file and convert it using containerized environment. Nobody can guarantee you 100% security at this moment but at least you are doing way more than majority of people.
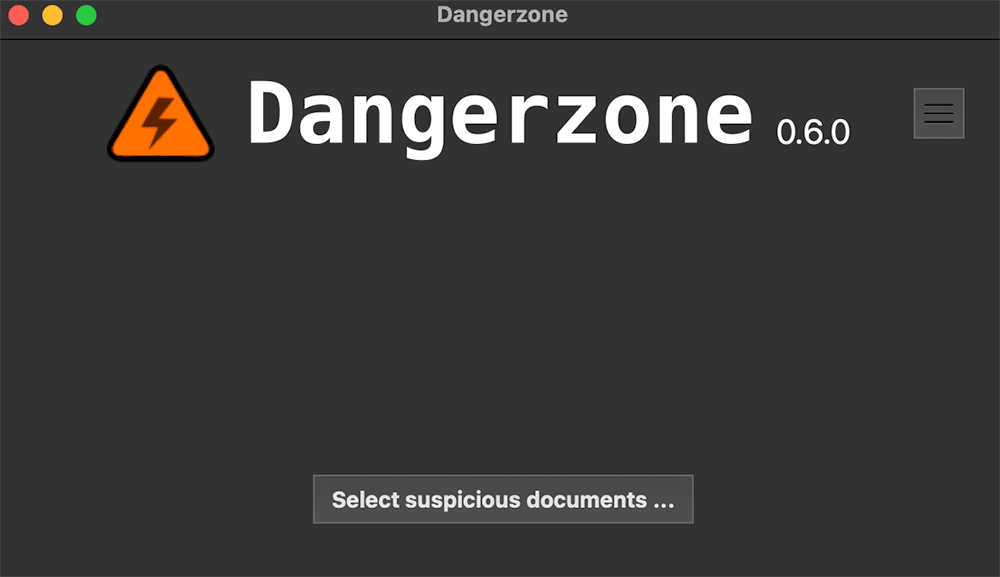
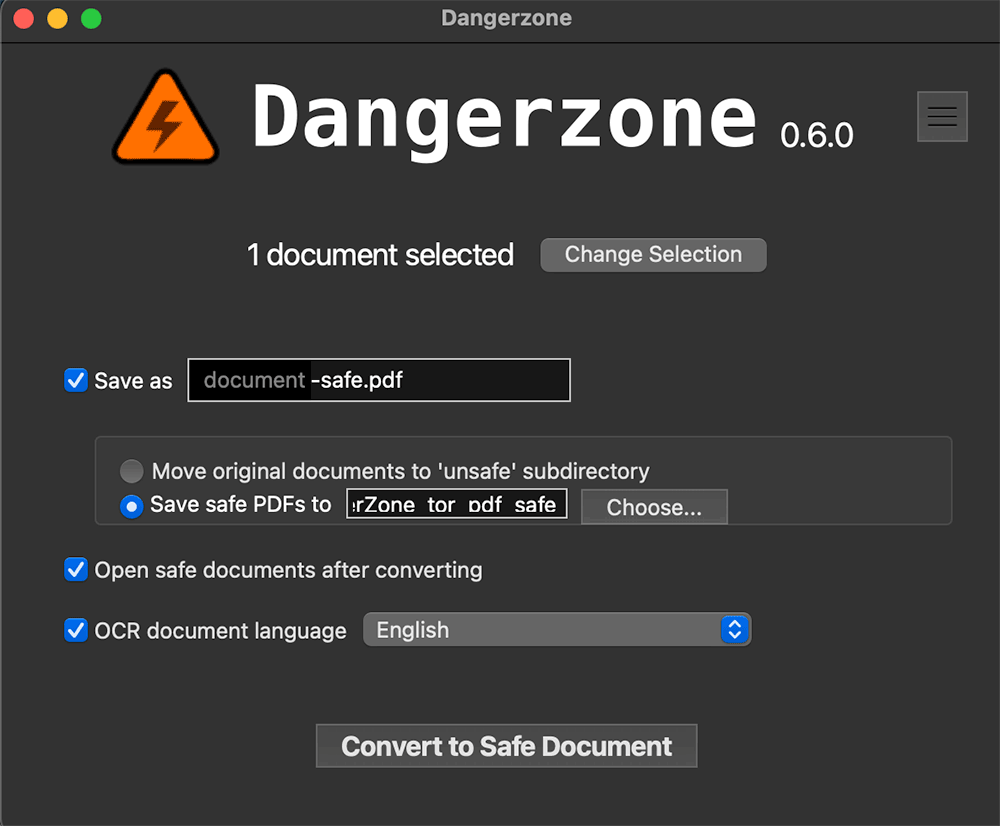
After conversion is done you are getting file with “-safe” suffix added and without embedded media. This is quite safer than before and of course non connection is being made to setup webhook.
5. Conclusion
In this knowledge article you got an idea how opening attachments and downloaded files can reveal your real identity even when you are initially connecting to network via TOR web browser.
Now you can implement hints and stay more safe.
Have a nice coding!